Private Connectivity in CircleCI
Connecting to private network resources from CircleCI
There are several options supported by CircleCI. Each Section outlines a manner for consideration, and trade-offs.
Example of the problem - by default most all customer networks block internet requests, including those from CircleCI workflows.
flowchart LR
internet
Customer_A_Network
Customer_B_Network
subgraph internet
subgraph Customer_A_Network
S[(Secure Resource, <br/> i.e. Database)]
end
subgraph Customer_B_Network
R[(Secure Resource, <br/> i.e. Artifact Repo)]
end
subgraph CircleCI SaaS Platform
C[CircleCI Orchestation]
A[Customer A Builds]<-->C
B[Customer B Builds]<-->C
end
H[Internet Baddy]--x|hacking| Customer_A_Network
A--x|Blocked|Customer_A_Network
B--x|Blocked|Customer_B_Network
end
There are different methods to achieve private connectivity with CircleCI, and selection should consider the caveats outlined for each.
IP ranges is a low-friction way to connect to your private network without opening firewall to the entire internet, but does not fully isolate your network.
flowchart TD
subgraph IP Ranges<br/>
subgraph X[Customer A Network]
S[(Secure Resource, <br/> i.e. Database)]
end
subgraph E[everyone else]
H[Internet Baddy]
end
subgraph CircleCI SaaS Platform
C[CircleCI Orchestation]
A[Customer A Builds]<-->C
B[Customer B Builds]<-->C
end
H--x|Blocked| X
A-->|Allowed|S
end
However IP ranges is not specific to the source organization within CircleCI’s environment. This means traffic from outside organizations could potentially connect to your network if additional authorization is not in place
flowchart TD
subgraph IP Ranges<br/>
subgraph X[Customer A Network]
S[(Secure Resource, <br/> i.e. Database)]
end
subgraph E[everyone else]
H[Internet Baddy]
end
subgraph CircleCI SaaS Platform
C[CircleCI Orchestation]
A[Customer A Builds]<-->C
B[Customer B Builds]<-->C
end
H--x|Blocked| X
A-->|Allowed|S
B-.->|Allowed|S
end
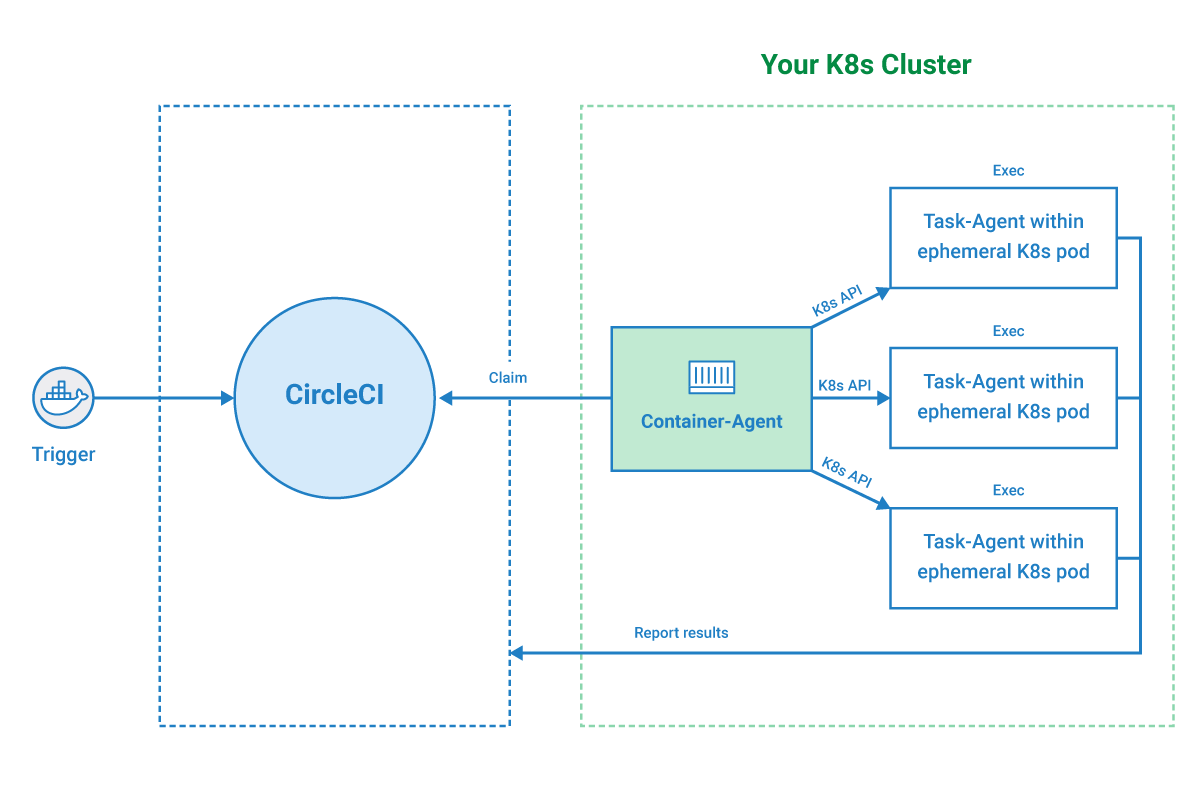
This is the most secure option as all communication originates from your environment making outbound connections to CircleCI’s orchestrator, retrieving any assigned work.
flowchart LR
subgraph Container Runner<br/>
subgraph X[Customer A Network]
S[(Secure Resource, <br/> i.e. Database)]
R[Runner]
R-->|Allowed|S
end
subgraph CircleCI SaaS Platform
C[CircleCI Orchestation]
A[Customer A Builds]<-->C
B[Customer B Builds]<-->C
end
R-->|Allowed|C
B-.-x|Blocked| X
subgraph E[everyone else]
H[Internet Baddy]
end
H-.-x X
end